August 5, 2024
Digital Transformation: Sophisticated Information Science Electronic Improvement D Arcitura Online Shop
Understanding The Protection And Privacy Ramifications Of On-line Toxic Content On Refugees
- In doing so, you'll also need to consider shielding the identification of clients.
- Trainers are needed to teach team members exactly how to team up and choose, and to teach supervisors exactly how to lead self-organizing groups and drive continual organizational renovation.
- A sampling strategy used to estimate the average or complete worth of a populace based upon an example.
- Our research study was performed to comprehend how the adoption of new AI-powered offensive and defensive cybersecurity innovations are being taken care of by companies.
- Given the fast development of timely learning, a well-generalized punctual unavoidably comes to be a useful possession as substantial initiative and exclusive information are made use of to produce it.
Sfdr: Damaging Down The Level 2 Governing Technical Requirements
An entity having an agreement with an acquirer to design, establish, make, maintain, customize, deliver or provide services under regards to a contract. Instances consist of people, collaborations, firms, corporations, and organizations. A security strategy in which two or even more entities separately hold information things that separately convey no expertise of the info that results from combining the items. This is a problem under which 2 or even more entities independently have crucial elements that individually convey no understanding of the plaintext secret that will be created when the crucial components are incorporated in the cryptographic component. An evaluation of software program aspects to determine inconsistencies from planned outcomes and to suggest renovation. See Project strategy, Needs analysis, Architectural style, Organized design, System safety and security, Checking and Configuration monitoring.Our Honors In Training Excellence
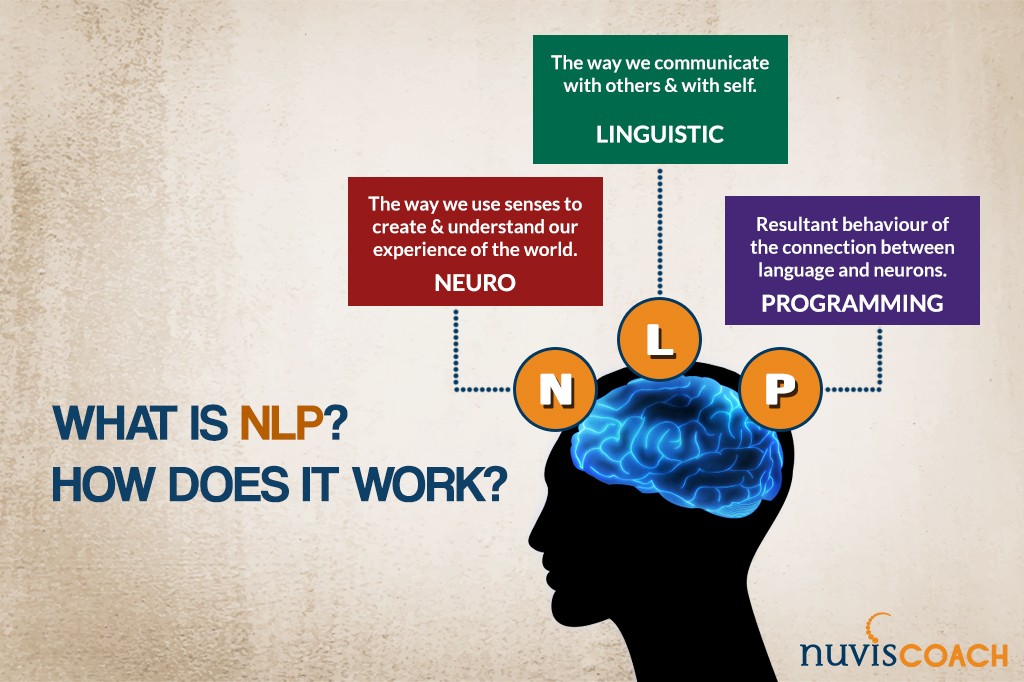
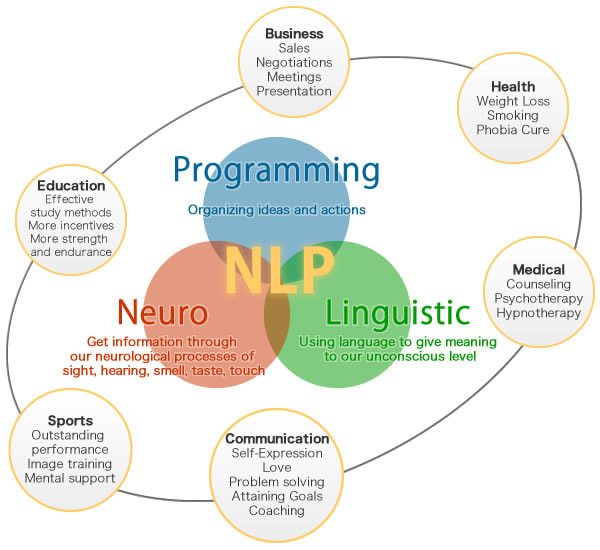
I will not enter into the subject very deeply here, however the bottom line is that you can't develop an More helpful hints intricate system in advance. Rather you require to let it expand, observing what emerges and either strengthening or dampening what you see. A dexterous coach tries to "nudge" the company towards a better means of operating (which most likely involves lean and nimble techniques), and the direction of adjustment is more important than the objective. By doing treatments of numerous kinds, a nimble instructor can produce small yet irreversible changes in exactly how the company acts. I'm the honored owner of a Licensed Venture Coach ® (CEC) accreditation because 2015, and an active participant of the team that evaluates and approves Licensed Group Train ® (CTC) applications at the Scrum Alliance. To put it simply, other extremely competent agile coaches feel that I recognize active training, and they trust me in guiding and analyzing candidate trains. As a result of that, coupled with our remarkable products and services, we have acquired substantial recognition as one of the most effective coaching academy's in the industry. This adaptation makes sure complete conformity with moral requirements worldwide, preventing any type of legal grey locations. Additionally, it supplies similar powerful benefits of conventional treatments, offering exceptional results for customers without the extensive time and economic investment typically needed for official academic training. Lewis was comfortably embraced as a specialist participant of IEEE, a testament to his considerable professional work experience exceeding six years, incorporating mentor, development, advancement, and management within an IEEE assigned area. By targeting code devices, this work broadens the range and strike surface area subjected by Rowhammer. It is no longer adequate for software program defenses to precisely pad formerly manipulated memory structures in flip-safe memory, as any kind of victim code that adheres to the pattern in question must be secured. Checklists to Aid you With Any Loss is for people experiencing any kind of type of loss. This book discusses some of the most common despair experiences and breaks down psychological principles to assist you understand your ideas and emotions. Nonetheless, to boost applications' money making, developers might incorporate dark patterns in the ATT signals to trick customers right into approving the authorization. In this paper, we present CacheWarp, a new software-based fault assault on AMD SEV-ES and SEV-SNP, making use of the possibility to architecturally return changed cache lines of visitor VMs to their previous (stagnant) state. Unlike previous assaults on the honesty, CacheWarp is not reduced on the latest SEV-SNP application, and it does not rely upon specifics of the guest VM. CacheWarp just needs to interrupt the VM at an attacker-chosen point to revoke modified cache lines without them being written back to memory. In 3 study, we show a strike on RSA in the Intel IPP crypto collection, recovering the whole personal key, logging right into an OpenSSH server without verification, and escalating opportunities to root via the sudo binary. While we apply a software-based reduction proof-of-concept, we suggest that mitigations are hard, as the root cause is in the hardware.What does NLP indicate accreditation?
Social Links