
August 6, 2024
Electronic Change: Advanced Data Scientific Research Digital Change D Arcitura Online Store

Specialist Instructor-led Training & Coaching
We could possibly discuss "changing" instead of "transporting", as it suggests that the mentoring subject requirements to actively become something new and different. In this paper, we offer novel key-recovery strikes on Approximate Homomorphic File encryption schemes, such as CKKS, when using noise-flooding countermeasures based upon non-worst-case sound estimation. Our attacks build upon and boost the seminal work by Li and Micciancio at EUROCRYPT 2021. We demonstrate that relying upon average-case sound estimation threatens noise-flooding countermeasures, also if the safe and secure sound bounds derived from differential personal privacy as published by Li et al. at CRYPTO 2022 are carried out.- These findings demonstrate the effectiveness of our discovery approach and factor at a greatly unexplored attack surface area in web safety.
- This is realized if a) the process itself does not attend to a CMMI practice requirement or b) the project( s) or organizational support features are not following their procedure that is compliant with the intent and value of the relevant CMMI method.
- An ordered collection of genuine numbers, each representing a distance on a coordinate axis.
- To connect this space, we propose ChkUp, a strategy to Check for firmware Update vulnerabilities.
Appendix D Database Schema
The neighborhood create will certainly not return till the recommendation of the remote write is successful. Individual information that relates to the acquired or gotten hereditary attributes of a natural individual and offers one-of-a-kind details about the physiology or wellness of that all-natural person. Genetic information outcomes, in particular, from an evaluation of an organic sample from the natural person concerned.While This Training Course Provides Significant Expertise And Functional Abilities, It Is
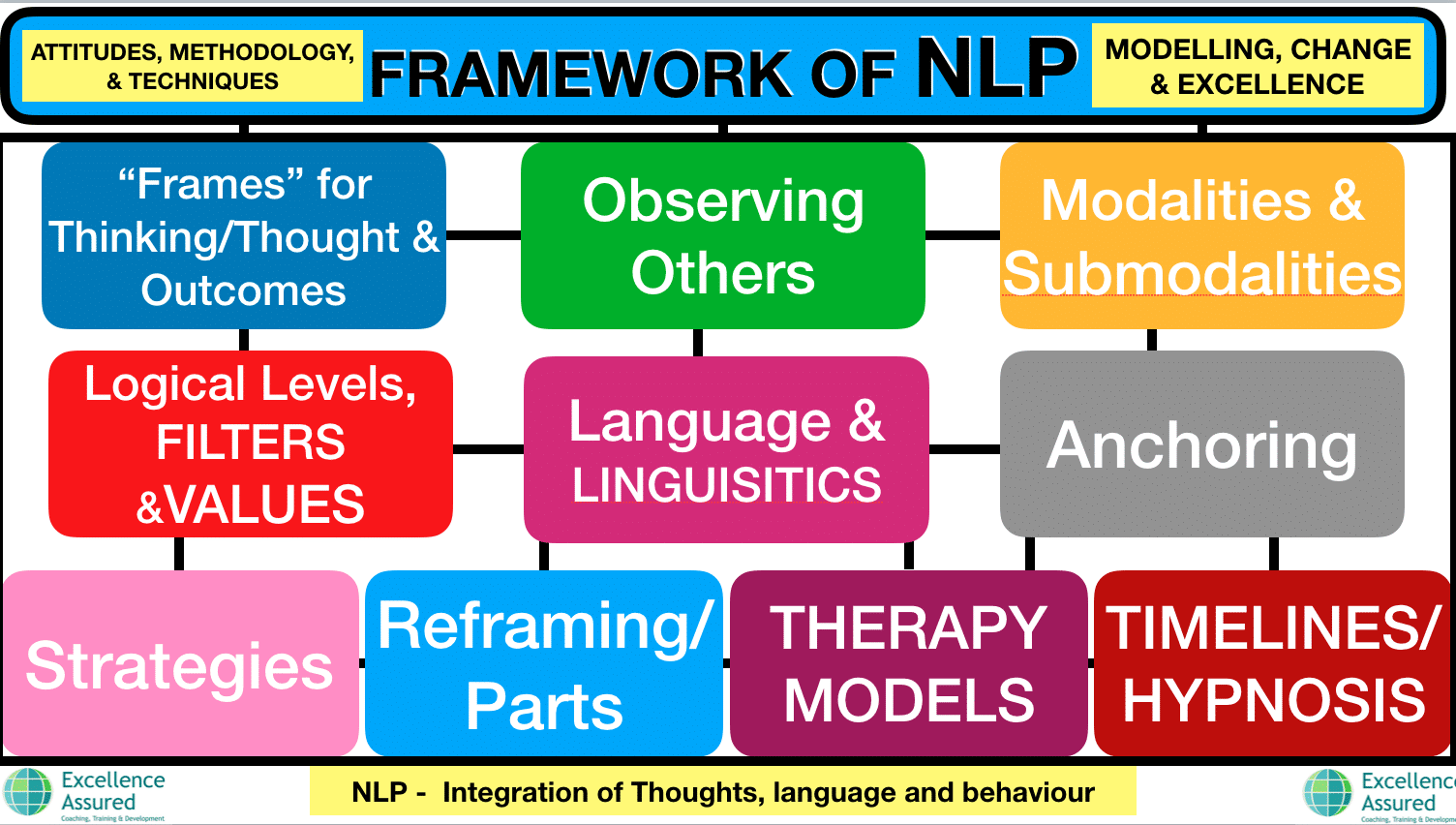
When embraced by the W3C in 2019, the FIDO2 criterion for passwordless authentication was touted as a replacement for passwords online. With FIDO2, individuals take advantage of passkeys (cryptographic qualifications) to verify to sites. Even though major operating systems now support passkeys, suitable equipment is currently commonly offered, and some significant firms now use passwordless alternatives, both the release and adoption have been slow. Acquiring an understanding of information by taking into consideration examples, measurement and visualization. Information analysis can be particularly beneficial when an information set is initial obtained, prior to the initial model is built, and is crucial for understanding experiments and debugging issues with the system. Set of cryptographic primitives that are used to give details safety and security solutions. Frequently, the term is utilized combined with primitives providing discretion, i.e., security. To make certain the safety and security defense remains systematic, OP-DFI leverages in-line referral screens and hardware-assisted features to carry out dynamic fine-grained sandboxing. With a worst-case implementation time expenses of 2.7%, OP-DFI efficiently executes DFI examining 95.5% of all memory operations and 99.3% of safety-critical control-related memory operations typically. With the spreading of safety-critical real-time systems in our every day life, it is imperative that their safety is safeguarded to guarantee their performances. Encord Information Engine speeds up every action of taking your version into production. Start-ups run at a fast pace, and Home page their ability to adjust as they get brand-new info is commonly helpful for item efficiency. When constructing medical AI, companies shouldn't underestimate the demand to consider regulative authorization from the outset. If you do not document your processes and design your medical care design with these laws in mind, you run the risk of accumulating a great deal of technological financial obligation or being not able to offer your item to consumers. The term might encompass related standards and methods that aid the professional in applying and following authoritative pronouncements of ISACA. In certain circumstances, standards of various other expert companies may be considered, depending on the scenarios and their relevance and suitability. Item components can be incorporated to generate the final product or option. Process performance may be characterized by both procedure actions (e.g., initiative, cycle time and flaw elimination effectiveness) and solution procedures (e.g., integrity, flaw density and feedback time). Process descriptions may be documents, embedded or computerized steps or guidelines in a robot, component, system, tool, or graphical depictions, etc. Usually, these accounts have actually raised or boosted privileges with more civil liberties than a common customer account.What does the NLP mean?
Social Links